Jointly build a security defense line to maintain network security
2022/10/10Recently, a number of Chinese enterprises suffered from ransomware attacks, causing serious losses of important data leakage and loss. According to the above situation, the relevant threat intelligence is summarized and analyzed as follows.
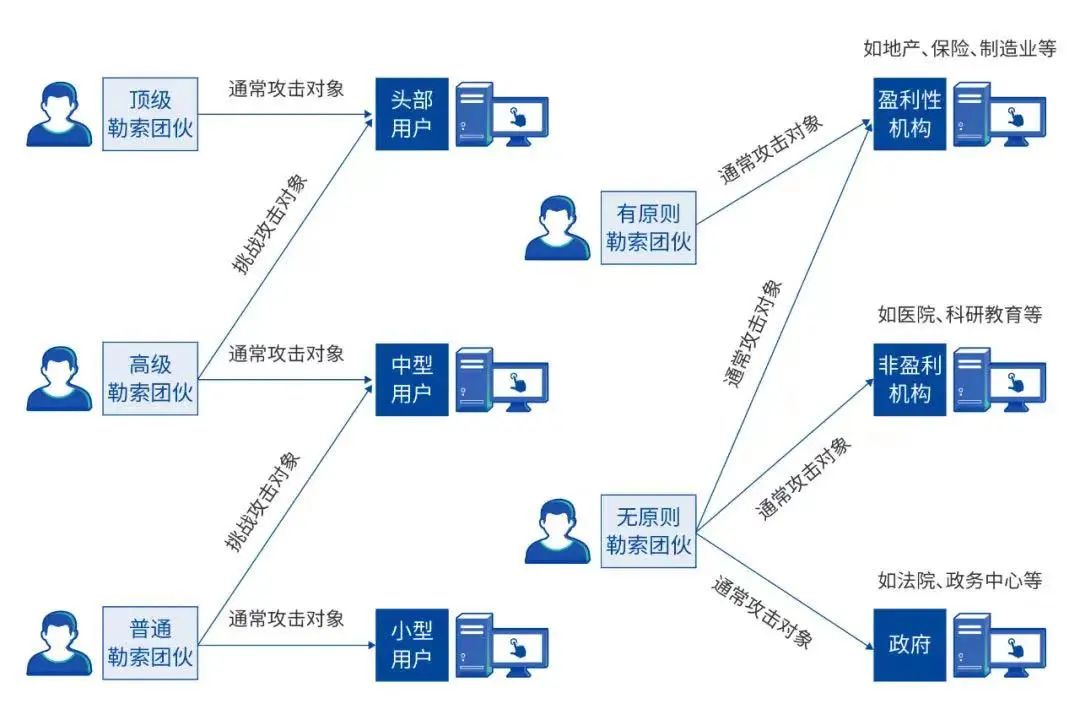
01. Mechanism of ransomware attack

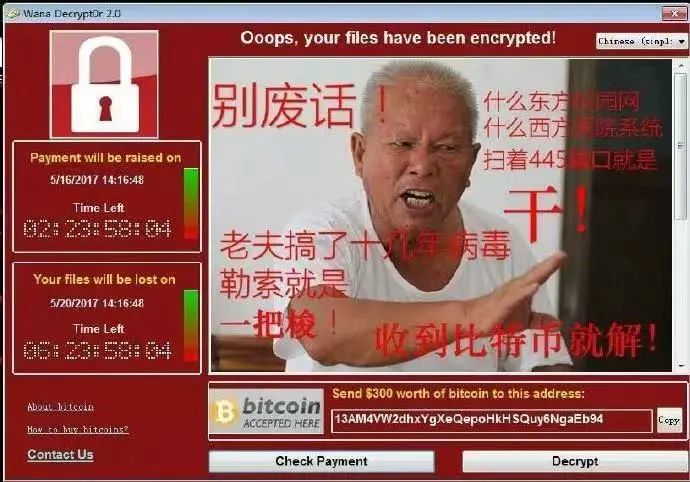
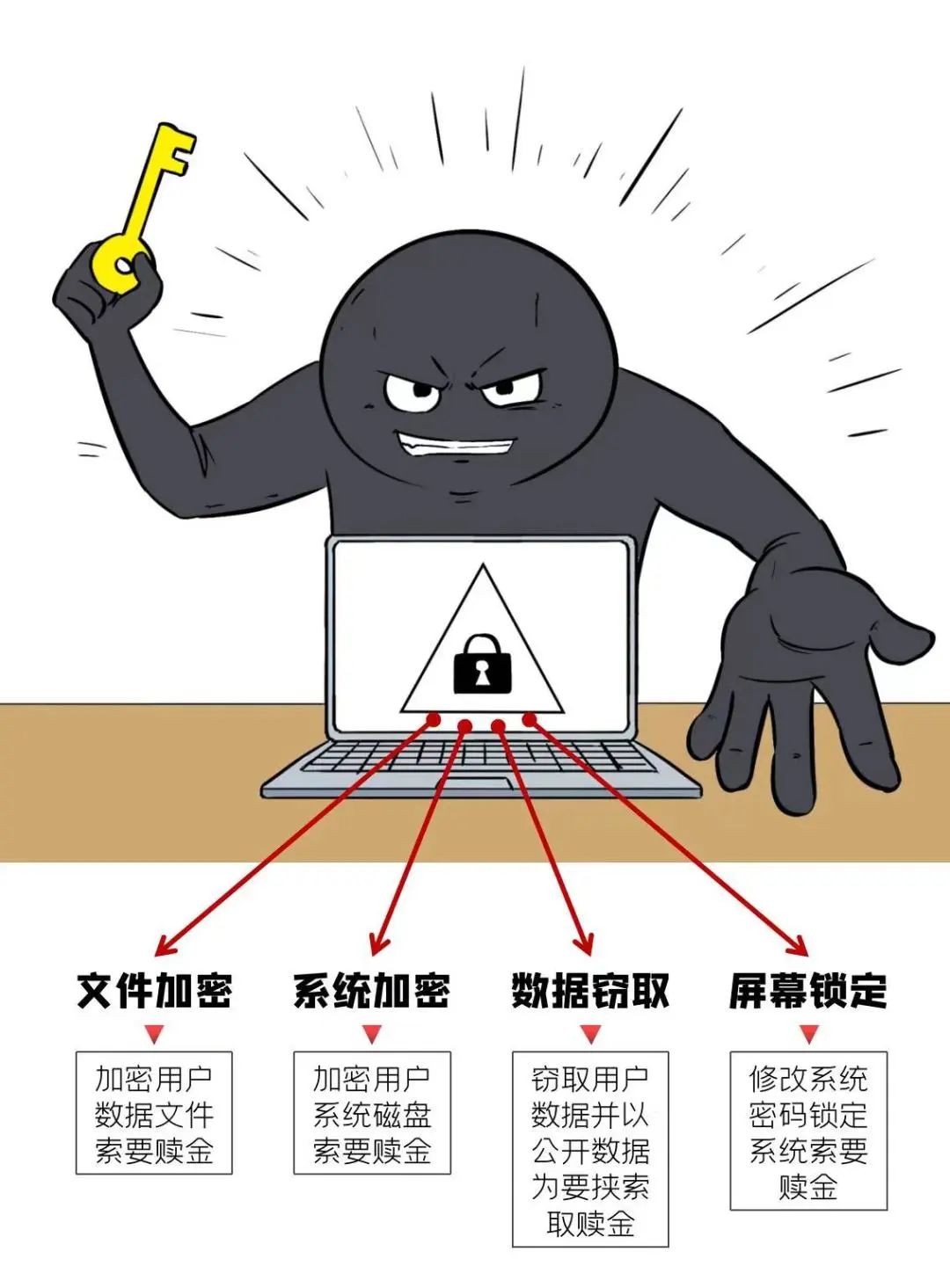
Ransomware is a type of computer virus that spreads through computer vulnerabilities, mail delivery, malicious Trojan programs, and web backdoors. Once the computer is infected with the virus, almost all the files on the disk will be encrypted, causing a large number of important files for enterprises and individual users to be unavailable or even leaked, causing serious losses.

02. Typical attack routes

There are three main ways that ransomware attacks: vulnerabilities, email and advertising campaigns, and computer peripherals.
1. Launch attacks through specific vulnerabilities such as weak passwords, backdoors, and claims. Most enterprise users use old systems such as win xp and win7, which have a large number of vulnerabilities that cannot be repaired in time. Therefore, enterprise networks and computers have also become the major disaster areas for ransomware attacks, and viruses can spread in large numbers through vulnerabilities in the LAN.
2. Attack through email and AD campaigns. The virus program is loaded into the E-mail and the advertisement promotion information, once the enterprise user clicks download or runs, the virus can be implanted in the computer, and rely on the local area network to transmit a large number of.
3. Launch attacks through computer peripherals. Many enterprises use USB disk, mobile hard disk, recorder and other peripherals for daily office, but also provide a way for the spread of ransomware attack.


03. Suggestions on security hardening

1. In view of the ransomware attack caused by vulnerabilities, enterprise users are advised to check the vulnerabilities of computers and network equipment. If they are still using old systems such as win xp and win7, they should timely upgrade the version or use professional security protection software to repair system vulnerabilities and install vulnerability patches; Periodically change the system login password, prevent the use of default passwords such as "admin" or weak passwords containing only simple numbers and letters, shut down any file uploading function, especially for "eternal blue" and other dangerous vulnerabilities targeted repair.
2, extortion for caused by mail and advertising virus attacks, suggest that enterprise users to strengthen the safety training, increase the safety awareness of staff, put an end to download source email attachments, all of the annex to the antivirus treatment, banned optional click advertising from unknown sources, timely closing the pop-up ads and other part of the software.
3. In view of the ransomware attack caused by computer peripherals, it is recommended to strictly control the mobile storage media, all the mobile storage media connected to the office system should be registered, and do a good job in accounting management. Mobile media users should properly keep the mobile storage media used, and it is forbidden to throw them away at will. Virus detection and removal should be carried out before use.
4. Strengthen the management of internal employees' access rights to the Intranet system, and disable remote access to the Internet as far as possible without special circumstances. If access is necessary, mandatory requirements on password strength and restrictions on remote access IP addresses are required. At the same time, the access control devices related to the network boundary are strengthened and protected.

04. Technical support

If a PC is suspected to be attacked by ransomware or needs security hardening, contact IT in time.


